Continuing from Stage3, now onto Stage4.
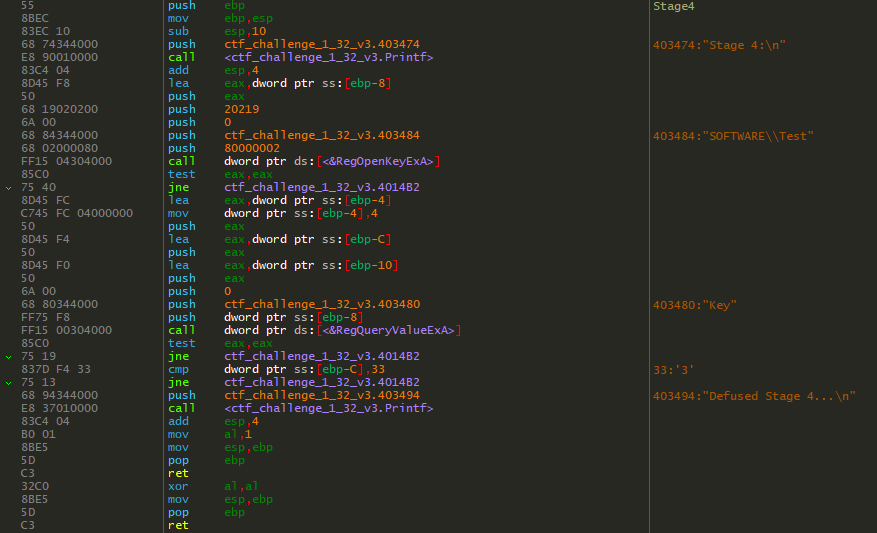
First there’s a call to RegOpenKeyExA which opens a specified register key. This call is returning with a value of 0x2 which is the error code for FILE_NOT_FOUND.
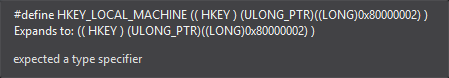
The first parameter of RegOpenKeyExA is a handle to a key, or it can be a predefined key. This call is using a predefined key because you can see its value in hex as 0x80000002. I didn’t have success in finding the values for predefined keys on Google, so I typed it into my IDE to get the value.
Now I believed it was trying to open a key at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Test but creating a key there was still leading to a return value of 0x2, or error code FILE_NOT_FOUND.
After some Googling I found my issue.
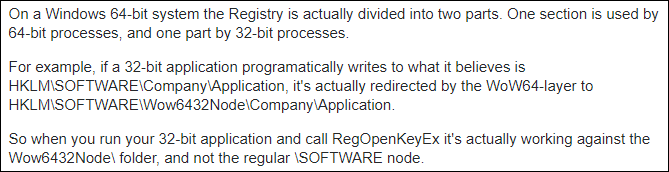
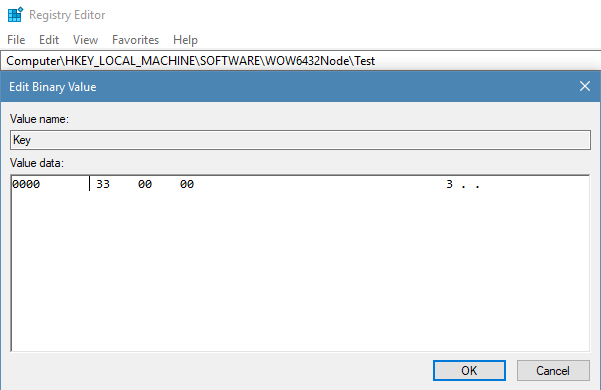
Very tricky! Now I knew to make my key at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Test using regedit. Now RegOpenKeyExAis returning a value of 0x0 which is error code ERROR_SUCCESS.
Next there’s a call to RegQueryValueExA which retrieves the type and data for a key with a specified name. The name of the key it’s trying to query is "Key". The value of the type is 0x1. It could be any of these types. To find out which one I started putting them in my IDE until I found which type is represented by 0x1.
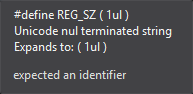
Now I know the type is REG_SZand the name is "Key". After RegQueryValueExA is called the data of the key is stored in a pointer. This pointer is checked to see if the data is equal to 0x33. I modified the binary data in regedit to 0x33.
And now I’ve successfully defused Stage4. Next up is the final stage, Stage5!
